
Securing the Sunshine State: A Guide to the Cybersecurity Liability Bill and NIST CSF 2.0
Did you know that 78% of publicly disclosed ransomware victims in Florida were local government entities, affecting cities, towns, counties, and school districts? With the ever-evolving cyber landscape, it can be difficult to stay ahead of threats even if you’re doing whatever you can to keep your organization secure. That’s why our Director of Advisory Services, Todd Atnip, hosted a webinar earlier this week diving into Florida’s proposed Cybersecurity Incident Liability House Bill and how NIST CSF 2.0 can help organization’s fall under its protection.
Note: This is a high-level overview of our webinar Securing the Sunshine State: The Cybersecurity Liability Bill and NIST CSF 2.0. For more insight into the framework and what it might look like for your organization, make sure to listen to the full recording here.
News from Florida
Todd started the webinar by giving a brief overview of recent laws and incidents that have occurred in Florida. Large organizations and cities have suffered from expensive ransomware attacks that cost hundreds of thousands of dollars to remediate. However, Florida government has introduced cybersecurity legislation, such as 2014’s Florida Information Protection Act, and updated legislation, like the legislation introduced in July of 2022 related to House Bill 7055. These updates included guidance around reporting requirements, paying ransomware demands, and required training.
These incidents and regulations of the past few years lead us to the main focus for the webinar, House Bill 473. This new legislation is intended to limit liability related to cyber incidents if public entities have implemented recognized information security framework controls (e.g., NIST CSF, ISO, HIPAA) to their standard operations.
Relevant Legislation
Below is a piece of HB 473 that is most relevant for counties, local municipalities, or related government subdivisions:
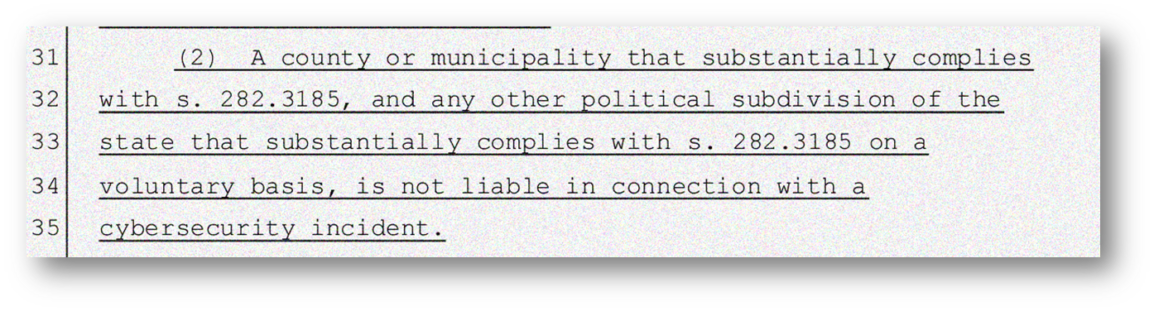
The key line to focus on here reads, “…is not liable in connection with a cybersecurity incident.” No one wants to be held liable for an incident that can cost millions of dollars, right? So, this bill functions as an additional incentive to comply with frameworks that will help you strengthen your security program. While attackers are only getting more brazen, this legislation will assist public, private, local, and state entities in Florida from falling victim to the cost of cybersecurity incidents as long as they comply with statute 282.3185.
s. 282.3185 states:
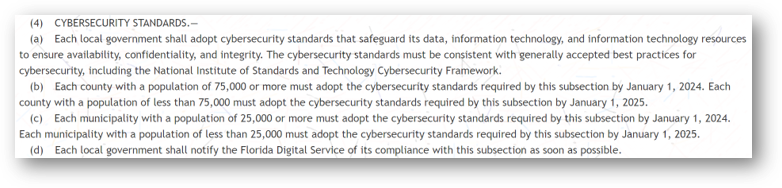
Our main focus in this statute is section (a). This is where NIST CSF is mentioned. Note that this section does not require entities to comply with NIST CSF specifically, however, there are some compelling reasons to use NIST as your chosen framework.
The NIST Family of Frameworks
Before delving into the reasons NIST CSF 2.0 is a great framework to comply with for this legislation, let’s take a look at where NIST CSF 2.0 falls in the NIST family of frameworks.
Below is a breakdown of the different NIST frameworks:
- NIST 800-53: This is the most comprehensive framework. If you are connecting to, authenticating into, and have authorization into federal systems, then you are probably required to comply with this framework at least at a moderate level.
- NIST 800-71: If you are subject to controlled, unclassified information as a private entity working with public, federal systems, then you are probably subject to this framework.
- NIST CSF: This is a voluntary framework intended to improve security. Previous versions of this were really intended for critical infrastructure, however, it’s grown since its genesis.
The Framework Landscape
Below, you’ll see a visual representation of some of the different frameworks displayed in a 2×2 matrix measuring scope of applicability and depth of coverage.
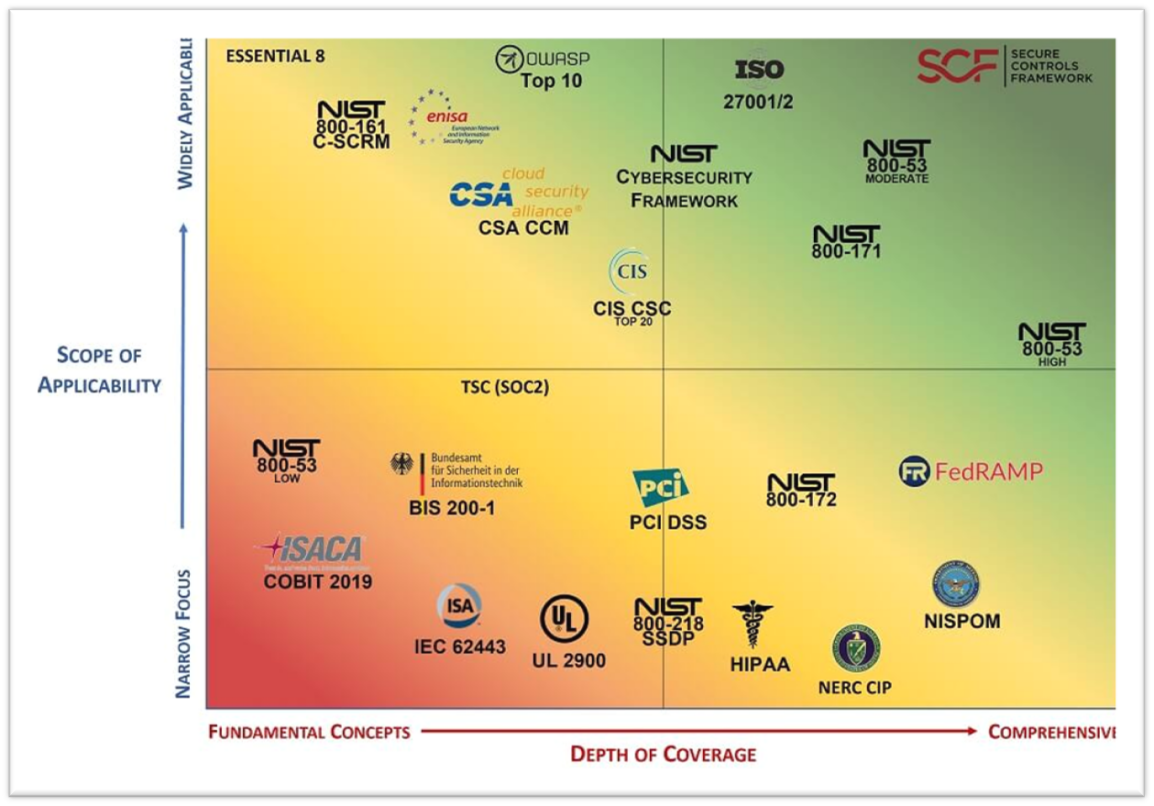
For context, you can see that the NIST CSF framework falls in the upper-middle area of the matrix, scoring high in its scope of applicability and moderate in the depth of coverage.
How accepted is the NIST CSF framework?
Keep in mind that because the newest version of NIST CSF (NIST CSF 2.0) was released in February of this year, much of this material relates to previous versions of the framework, but 2.0 is an improved version of the framework.
Adoption of NIST CSF is growing. Businesses, governments (both state, county, and municipality level), as well as other types of organizations have adopted the NIST CSF. Tenable did a study in the last few years on the adoption of NIST CSF. From this study, we can learn that about 30% of all organizations had adopted NIST CSF at some level. Of those 30%, 70% of those organizations considered NIST CSF a best practice framework. When asked how likely organizations were to adopt NIST if they weren’t already using it, 50% of respondents said that they would seriously consider NIST CSF for future cybersecurity efforts.
Another point to note is that NIST CSF is a collaborative framework; it’s not governed by a cybersecurity governing body like PCI or AICPA. NIST CSF is a collaboration between cybersecurity leaders and various types of organizations. What this means is that it uses a common language to address and manage cybersecurity risk in a cost-effective way based on business needs without placing additional requirements on businesses. This framework allows a way to speak to everybody at all levels of the organization about outcomes that are considered best practice without going into highly technical language.
Finally, NIST CSF is a technology agnostic framework, meaning there is no endorsement of discussion in the framework about using a specific type of technology. There’s a lot of flexibility in how things are done within the framework.
How NIST Is Different from Other Frameworks
As mentioned above, NIST does not have a governing body like the SOC, ISO, and PCI frameworks, so there are not the same requirements for meeting certain standards. Because NIST CSF is voluntary, there are not requirements for testing and implementing controls in a certain way.
The NIST CSF framework isn’t necessarily about what you do and certainly not about how you do it, but its main focus is on outcomes. What are the outcomes on the practices you should be doing? What does good look like? When you focus on what good outcomes look like, then you can backtrack into the “What?” and the “How?”.
Secondly, NIST CSF is very focused on managing risk of both information security risk management (data) and cybersecurity risk management (infrastructure, processes, technology, cybersecurity personnel). If you haven’t done a good job managing and understanding risk comprehensively in the organization, then how do you know the controls that you put in place are adequate? NIST CSF 2.0 places a lot of focus on this.
Implementing NIST CSF
The implementation of NIST CSF works off of the idea of tier profiles according to six functions that help determine an org’s current and target tier profiles.
(For more on tiers and tier implementation, make sure to watch the full webinar recording!)
The 6 functions are:
1. Govern
2. Identify
3. Protect
4. Detect
5. Respond
6. Recover
Organizations can either self-assess or have a third party asses what tier profile they fall under. This is your current state.
The second thing you would do is determine your target tier profile, or what tier profile you’d like your organization to fall under. The difference between your current profile and your target profile is the gap. Gap assessments help determine how an organization can get to their target profile.
The six functions pretty much cover the whole of cybersecurity. Most organizations need work in at least one of these categories, but by looking at the language surrounding these functions, you’ll be able to tell what tier your organization falls into. From here, you’ll be able to determine what best practices you can put in place to improve your security posture, such as sharing your organization’s mission and goals regarding cybersecurity, so everyone is on the same page.
In the webinar, Todd provided a compliance roadmap (steps seen below) that can help with the implementation of NIST CSF 2.0. Implementing NIST CSF is a crucial step for any organization to ensure their cybersecurity risks are managed effectively. The seven steps included in the roadmap involve understanding the organization’s business objectives and potential risks, conducting a comprehensive risk assessment, developing a risk management plan, implementing security controls, monitoring and assessing security controls, developing and implementing response plans, and continuously improving the cybersecurity posture.
However, compliance is never done, so regular reviews and updates are necessary to adapt to evolving risks. By following these steps, organizations can mitigate potential threats, reduce their cybersecurity risks, and protect their critical assets, data, and systems.
The steps to the compliance roadmap are:
- Understand your business objectives and cybersecurity risks
- Conduct a risk assessment
- Develop a risk management plan
- Implement security controls
- Monitor and assess security controls
- Develop and implement response plans
- Continuously review your cybersecurity posture
Why NIST CSF 2.0?
Now that we’ve talked a little bit about how NIST CSF 2.0 is structured, let’s recap some of its benefits.
- Builds trust with partners and stakeholders
No matter the framework, you want to build trust with your constituents, partners, and stakeholders.
- Comprehensive guidelines for cybersecurity controls
NIST CSF 2.0 provides the outcomes that you should have with cybersecurity controls in place. This framework isn’t just one small area of cybersecurity. It covers everything: technology, people, facilities, supply chain, intellectual property, and more that you need good outcomes for.
- Organizational resilience
NIST CSF 2.0 is a framework you can adopt. If you put a majority of the framework in place at some tier level, then the chances that you’re not going to be able to deliver services is much lower.
- Integrated risk management approach
The idea of continually revisiting your risk management approach means that you’re always thinking about aligning your risk with the controls that you have in place where you’re not doing too much or too little.
- Flexibility in the “How?”
If you’ve already got a lot of controls in place and you just want to reconcile those with the CSF, it doesn’t mean you have to go in a different direction than what you’ve been doing. Since there’s no specification in the framework about what tool set you have to use or what ideas have to be put in place, some of what you’ve already done may be applicable to the framework.
Partner with KirkpatrickPrice to Help Secure the Sunshine State
Tackling a new framework can be challenging even if it will help your organization reach its security and compliance goals. We hope this webinar recap helped you understand how NIST CSF 2.0 can help you fall under the protection of Florida cybersecurity legislation, but if you have questions about this framework or about how certain legislation will apply to your organization, connect with one of our experts today. We’d love to help you succeed.