
Creating Effective Network Diagrams and Data Flow Diagrams
The Importance of Network and Data Flow Diagrams
Network diagrams and data flow diagram are called out in PCI Requirement 1; in fact, the PCI DSS puts so much weight on a good diagram that they include it in the first phase of the Prioritized Approach, which is the recommended method to remediate compliance gaps.
But, PCI is not the only place where network and data flow diagrams are valid. In any environment where an organization has sensitive data, these two pieces of documentation are critical during an audit. They will provide valuable information and understanding about the environment in less time than any other piece of documentation. So, how can you create effective network diagrams? How can you create effective data flow diagrams? Let’s discuss.
What is a Network Flow Diagram?
A network flow diagram maps the flow of data through networks. Digital systems often involve network-connected systems with functionality distributed across multiple nodes. For example, in an ecommerce store, data might move from an order system to invoicing, payment, and logistics systems.
A network flow diagram indicates the routes over which data travels, the internal and external nodes on which it is stored or processed, and the purpose of those nodes. Network flow diagrams are essential to understanding the environment that hosts sensitive data as well as risk mitigation and the enforcement of information security policies.
How to Create Effective Network Diagrams
Effective network diagrams show where sensitive data is on your network and how it is protected. In order for a network diagram to be effective, it needs to achieve the following:
- Identify:
- All boundaries of the sensitive data’s environment
- Any network segmentation points which are used to reduce scope of the assessment
- Boundaries between trusted and untrusted networks
- Wireless and wired networks
- All other connected points applicable to the protection of sensitive information and the critical assets where it is transmitted, processed, or stored
- Locate the network protections (i.e. firewalls, IDSes, router ACLs, etc.) surrounding the systems that transmit, process, or store the data in question (the “sensitive environment”). Important considerations include:
- Define the boundaries between trusted and untrusted networks, including any network segmentation related technical controls that enforce segmentation if the entire network is not supposed to be in scope.
- If there is no internal network segmentation, then your entire network is in scope for the audit.
- VLANs do not, by themselves, constitute internal segmentation since they don’t restrict access.
- Internal segmentation might include internally deployed network firewalls; router ACLs that only allows specific devices to communicate to the sensitive systems; Network Admission Control or similar technology to make decisions on whether or not a device requesting access to the sensitive area has met the security requirements such as patch levels, anti-virus signature dates, and last scan time, etc.
- In all cases, segmentation must enforce access to the sensitive areas. If a packet – any packet – can get from one place to another, then the source is not segmented from the sensitive environment and it is in-scope.
- Identify ALL wireless networks – even if they’re out scope.
- Identify the system components involved in transmitting, processing or storing sensitive data. This includes workstations, databases, routers, firewalls, wireless access points, application servers, switches, etc.
- Identify the devices responsible for administering the security of the sensitive systems (i.e. antivirus, logging, authentication, etc.).
How to Create Effective Data Flow Diagrams
In a simple environment, the data flows might be easily overlaid on top of network diagrams. In more complex environment, you might see something else altogether. We frequently see “swim lane” flowcharts that break the process down into “lanes” executed by specific teams. The form and structure is less important than the information contained in it, though. Effective data flow diagrams must include the following:
- Be sequenced. For example, “We receive sensitive data at X; it goes through these Y points and is destroyed at Z.”
- Follow the data life cycle.
- Create: Where does data come into our organization? What business processes – such as a sales team or a call center – are involved? What technical systems – such as a web server, an SFTP server, or contact center – are involved?
- Share: With whom and how is the data shared? For example, by email attachment, SharePoint, or AWS S3 bucket.
- Use: What people and system components use the data – either as input or provided as output as part of the process?
- Store: Where is it stored? A filing cabinet, a shared folder?
- Archive: How, where, and for long is the data archived? For instance, archived in an S3 Glacier bucket for one year, on magnetic tape for two years, then in a records warehouse for seven years.
- Destroy: How is it destroyed when no longer needed? Is it via Iron Mountain shredding service, by secure electronic wipe of the magnetic tape?
- Have sufficient references to names of applications where sensitive is transmitted, processed or stored. The application details, including the system components on which it runs, might be documented elsewhere in a more complex environment.
- Address the question: Where is my sensitive data and who needs to interact with it?
An Example Network Flow Diagram
Whether you’re undergoing a PCI or SOC audit, or you’re pursuing other compliance goals, creating and maintaining effective network diagrams and data flow diagrams is key to your audit success. Because we know that this is complex but critical documentation, KirkpatrickPrice auditors are committed to helping our clients create thorough network diagrams and data flow diagrams.
Our client, Net Friends, is a great example of this. After Net Friends’ SOC 2 audit, they commented,
“We are so appreciative of the time and attention we received from Randy and the team at Kirkpatrick Price during the SOC 2 audits, and their collaborative approach of working with us on topics that extend well beyond their core mandate. Who could have predicted when we started this ongoing audit process that we would be inspired creatively?!?”
This is part of KirkpatrickPrice’s mission – to inspire and empower our clients to achieve challenging compliance goals.
Here’s an example network flow diagram we put together for Net Friends’ before and after:
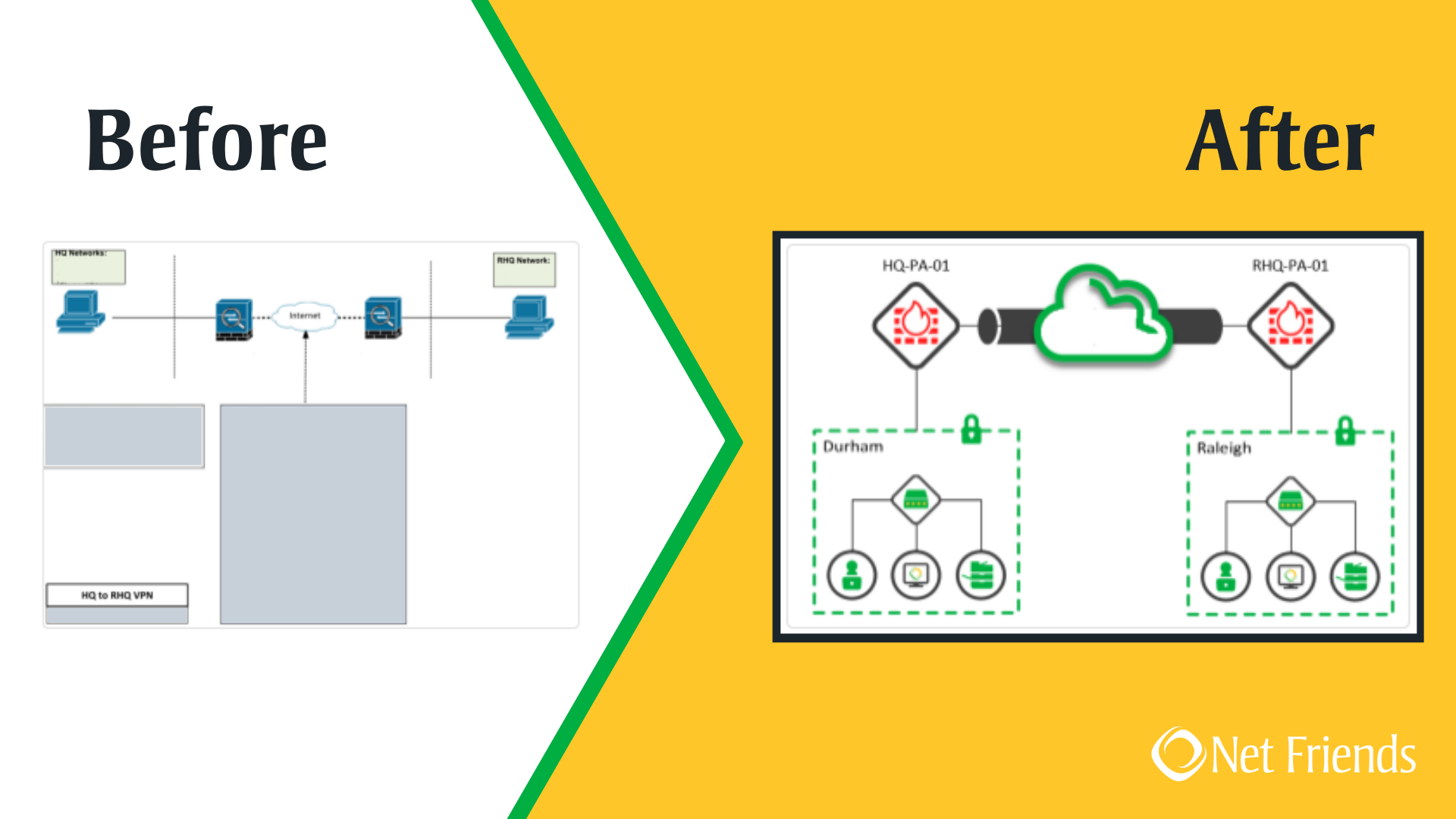
All in all, effective network diagrams and effective data flow diagrams play off of each other. They are powerful tools that will provide significant amounts of information to those responsible for protecting sensitive data. They will help you define scope the of affected system components, identify critical controls, and identity weaknesses in the control framework. If you want to learn more about how KirkpatrickPrice can help you improve your network diagrams and data flow diagrams, contact us today to speak to a specialist.