
How Mobile Devices Impact Protected Health Information
The use of mobile devices has absolutely transformed healthcare. Have you ever checked into a walk-in clinic on a tablet? Has a doctor shown you X-rays through a digital screen, rather than on film? Have you paid a medical bill through an app? Mobile devices are altering patient care. The need for mobility in healthcare settings is pervasive and the security threats that mobile devices pose are only going to proliferate. Think about all the elements that support mobile devices in a healthcare setting. Servers, networks, data storage, policies – the list goes on and on. As technology advances, so does the threat landscape. Mobile devices present many advantages to healthcare, especially to patient care, but they do impact protected health information.
The Need for Mobile Devices
In any type of healthcare setting, consider the vast amount of tasks that can be completed using mobile devices. Patient management, record maintenance, time management, information gathering, dictation, clinical decision-making, administration, education – it can all be done through tablets, laptops, smartphones, etc. Mobile adoption has replaced pagers, charts, X-rays, calculators, and other formerly key aspects of healthcare.
On a personal level, mobile devices are a must-have. You can bet that any healthcare professional you interact with has a personal mobile device on them. How does this impact your PHI? Well, what controls are set up so that they cannot access PHI from a personal mobile device? What does the organization’s proper usage policy state; when can they use their device while in the workplace? Mobile devices are pervasive in healthcare settings, especially when the majority of employees are walking around with one in their pocket.
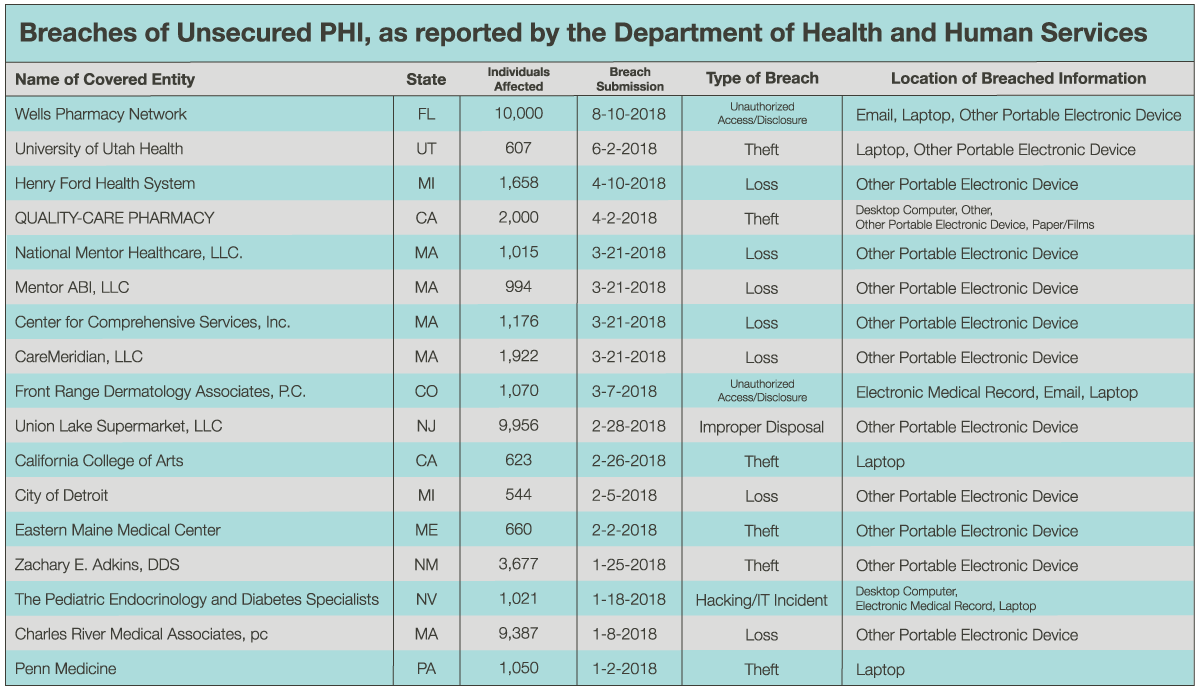
Data supports the notion that mobile devices require different controls than other devices, like a printer or scanner. According to the Department of Health and Human Services’ HIPAA breach portal, or “wall of shame,” over 45,000 individuals have been impacted so far this year (January 1-September 1, 2018) by a breach of a mobile device. Note that these are only reported breaches to date this year; who knows how many have gone unreported. While hacking, improper disposal, and unauthorized access are factors, the majority of these incidents are due to theft or loss. This highlights the fact that physical safeguards are a major component of securing mobile devices.
How to Safeguard Protected Health Information
Because HIPAA covers the smallest of healthcare providers to the largest health plans in the country, the Security Rule is scalable. It doesn’t require specific technological solutions, but rather, requires organizations to implement reasonable and appropriate security measures to protect PHI and ePHI in their daily operations.
HIPAA Mobile Device Security Policy
- If a covered entity allows staff to use smartphones as part of its BYOD policy, the organization would need a mobile device management policy. This approach gives control to PHI at all times and provides secure applications. This policy would require organizations to keep a list of all devices and personnel with access to the device, create a method to determine the owner and purpose of the device, and document authentication for the use of the device. It could also provide a remote wipe capability in case of a lost or stolen device.
- In a BYOD policy or a company-owned mobile device plan, organizations should develop a usage policy. If usage policies are not implemented, personnel could use mobile devices in a way that violates company policy, allowing malicious attackers to gain access to critical systems and PHI. Use PCI Requirement 12.3 as reference for the basics of a usage policy.
- A policy for access and privileges based on business need to know is a smart choice for HIPAA compliance. This is a more technical policy that limits who can access PHI and makes access trackable, in case a breach does occur and you need to trace the source.
- While HIPAA doesn’t require encryption, it’s another way for covered entities to secure the use of mobile devices. Encryption allows an organization to convert the original form of information into encoded text, making the information unreadable unless an individual has the necessary key to decrypt it.
The National Cybersecurity Center of Excellence developed Cybersecurity Practice Guide SP 1800-4, which provides other best practices for safeguarding PHI when using mobile devices. As you develop safeguards to protect PHI during the use of mobile devices, remember that mobile devices require different physical security controls than other devices and in-depth usage policies.
Are you unsure if your policies protect PHI during the use of mobile devices? Want to learn more about HIPAA compliance obligations? Contact us today to begin your compliance journey.
More HIPAA Resources
Using the NIST Cybersecurity Framework to Protect PHI
Managing Business Associate Compliance