
Threat Informed Defense (Part 1): Threat Simulation [A Webinar Recap]
Cyber threats pose significant risk to organizations worldwide, ranging from financial loss to reputational damage to operational disruptions. These ever-evolving threats can be intimidating, but with the right preparation, organizations can proactively mitigate risks and fortify their overall cybersecurity posture. One way to offensively protect your organization from the treat landscape is through threat simulation.
This week, our VP of Pen Testing, Jason Rowland, kicked off our three-part Threat Informed Defense webinar series with the first session which focused on Threat Simulation.
Note: This is a high-level overview of our webinar Threat Informed Defense (Part 1): Threat Simulation. For more insight into this topic and what threat simulation might look like for your organization, make sure to listen to the full recording here.
What is threat informed defense?
Before diving into the details, Jason took a moment to define a couple of important terms.
MITRE Enginuity’s Center for Threat-Informed Defense notes that, “Threat-informed defense is the systematic application of a deep understanding of adversary tradecraft and technology to improve defenses.”
In simpler terms, threat-informed defense encourages us to understand the adversaries that are most likely to impact our environment; understand the tactics, techniques, and procedures (TTPs) those adversaries employ in infiltrating our environments; and shape our defenses around those TTPs.
Leveraging knowledge of cyber threats to prioritize the allocation of limited resources is one of the most impactful and efficient ways to reduce overall risk.
Threat-informed defense is possible because of ATT&CK. MITRE ATT&CK is a curated knowledge base for cyber adversary behavior that focuses on the why (tactic) and the how (technique) of adversary actions. Over the last ten years, as we’ve learned how adversaries both break into and move through our environments as well as how they ascertain, those techniques have been captured in the ATT&CK framework. The ATT&CK framework also gives us a common taxonomy to talk about adversary actions. It’s a way for red teams and blue teams to communicate using the same terms.
Follow this link to check out the MITRE ATT&CK framework.
Fundamentals
The purpose of threat simulation is to help you understand your cybersecurity effectiveness. Organizations may ask: Are our people trained and alert when it comes to security threats? Are our internal security processes effective? Are technology investments configured correctly and delivering value?
If you’re asking yourself these questions, you’re not alone. These questions are so common that they supported an entire industry built around cybersecurity assessments. There are several different testing approaches used in offensive security, like red team engagements, vulnerability assessments, and penetration tests to name a few. All of these assessments help network owners better understand their security and make improvements in defending against threats. Threat simulation is additive to these methods. Each of these offensive security techniques has its time and place.
Why do new testing methods continue to be created? The reality is that while these other assessments are good to do, they are not always representative of real-world threats. For example, traditional penetration tests and vulnerability assessments often focus overwhelmingly on identifying and mitigating initial access vectors, meaning these tests say very little about the hundreds of post-exploitation TP’s spanning the attack matrix. Therefore, the way that real-world adversaries operate is fundamentally different than how we operate during traditional cybersecurity assessments.
What is threat simulation?
Threat simulation is an intelligence driven discipline that entails researching, modeling, and executing cyber adversary tactics, techniques, and procedures to assess and improve cybersecurity. Threat simulation is about understanding what threats exist with the means and motive to come after your organization and the data that you’re responsible for. Pen testers want to research and model those threats to understand how the threats work inside of an environment.
A primary characteristic of threat simulation is that the TTPs are meant to emulate adversary behaviors commonly seen in the wild. This method ensures that defenses can be tuned to real-world threats. Different industries are facing different threats, so threat simulation takes those real-world threats that are probable for a certain industry and works to defend against them.
Another main focus of threat simulation is tuning defenses around behaviors that are difficult for adversaries to alter as opposed to tuning around fragile signatures like has values and IP addresses. When threat simulation is based off of the TTPs, testers force the bad actors to change the way they conduct their operations.
Threat simulation is also typically transparent, meaning that the testers fully disclose what the red team did in as much detail needed for the network defenders to improve their defenses. Adversary emulation is also collaborative, meaning the testers work with the defenders to effect positive improvement.
Threat Simulation Framework
The threat simulation framework is how the pen testers will conduct a threat simulation engagement.
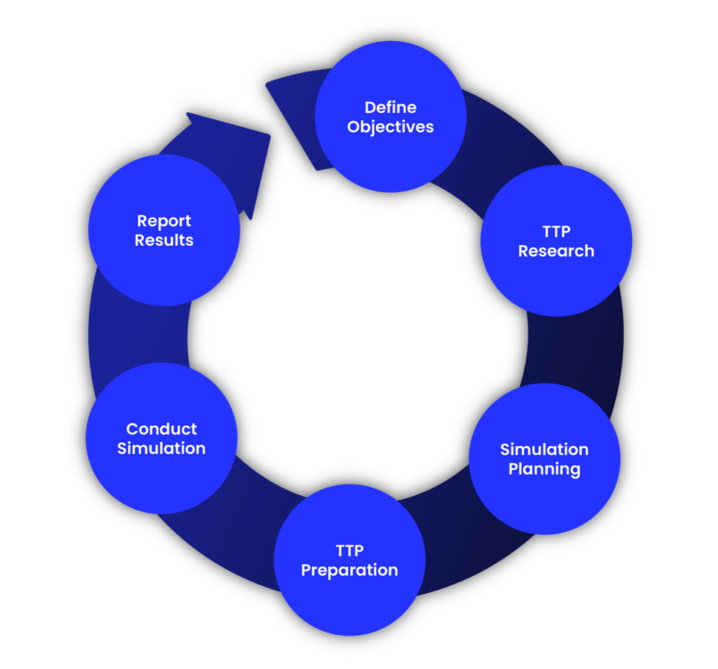
1. Defining Objectives
Defining the objectives of the simulation is an important first step in the framework. This step will be highly dependent on the industry that you’re in, your business model, and the threat landscape at the time of conducting the exercise.
2. TTP Research
Adversary Research
In this step of the framework, you need to select adversaries and/or TTPs to research that are relevant to your organization. It’s important to align this step with your cybersecurity objectives. The requirements of adversary research are understanding the threat landscape and how it relates to your business. Researching adversaries should not be arbitrary. This step takes a lot of time, so you need to make it worth it by conducting good, relevant research.
Internal Research
Internal research involves discussing what cyber threats the internal teams are concerned about and reviewing past incidents. Important teams to include in this research are the threat intel team and network defenders/system administrators. In this step, it’s beneficial to look at past incidents and see how you’ve remediated those issues. Many companies get attacked in the same way multiple times.
External Research
External research can be done by accessing publicly available information, such as ATT&CK/Tidal Cyber Community, CTI article, and industry reports (Verizon Data Breach Report). However, when you’re conducting external research, be wary of headline bias when selecting threats.
How do you know when your TTP research is complete? Initial research is usually done when you have a short list of threat actors or techniques that align with cyber security goals, and you can clearly communicate their relevance. It’s important that you know how to move forward, and you know how to communicate that strategy to the organization.
Threat Selection Considerations:
- Relevance
Make sure your TTPs are aligned with your business.
- Available CIT
Testers need enough CTI to replicate a certain threat. If there’s not enough CTI, it may not be a threat that is eligible for this exercise.
- TTP complexity
Make sure you have the time, staff, and expertise to replicate a certain threat.
3. Simulation Planning
Planning for your threat simulation is an essential step to this framework. Threat simulation can cause significant issues if not properly planned, such as disclosure of sensitive data, data loss, and unplanned downtime, not to mention that executing adversary TTPs without permission will very quickly land you in trouble. Proper planning is essential to a successful adversary emulation engagement.
So, what’s the best way to plan for a threat simulation? Threat simulation planning generally includes documenting the following:
- Engagement objectives
It’s important to be able to describe and document the relevance to your organization and why you’re taking on the TTPs.
- Scope
In this context, scope identifies organizations, users, and/or devices upon which adversary emulation activities are permitted, like organizational units, users, and devices. In this step of the planning, testers need to work with network owners and system administrators to identify and document devices that are in scope. Network diagrams can be helpful in this step as long as they are accurate. You’ll also need to identify high-value assets and the assets specifically out of scope.
- Schedule
The schedule defines dates and times in which adversary emulation activities occur and when deliverables are due. This step of planning is important for deconflicting adversary emulation activity against legitimate business operations and identifying periods in which adversary emulation activities should not occur.
- Rules of engagement (RoE)
What TTPs are permitted? What mitigations can be applied for high risk TTPs? The Rules of Engagement document defines acceptable adversary emulation behavior. This is the time to talk through sensitive situations. You’ll need to discuss cohabitation of malware, deviation from approved scope, disclosure of sensitive information, and observed illegal or unauthorized activity.
- Permission to execute
Pen testers always need to get explicit permission to conduct the adversary emulation activity from the network owners, but first, testers need to make sure they have sufficient authority to authorize the engagement. Testers should never assume they have the authority to practice adversary emulation in a network they don’t personally own, otherwise, they risk serious legal and/or criminal action.
- Communications plan
The communication’s plan describes how the threat simulation team will communicate with the network owners. Everyone needs to agree on a time and how often that communication should occur. Another important item to discuss in this step of planning is whether the engagement will be collaborative, like a purple team, or will it be opaque/black box?
4. TTP Preparation
TTP implementations form the substance of threat simulation. This step in the framework provides a trusted means to execute adversary behaviors and enables testers to tune defenses around adversary behaviors.
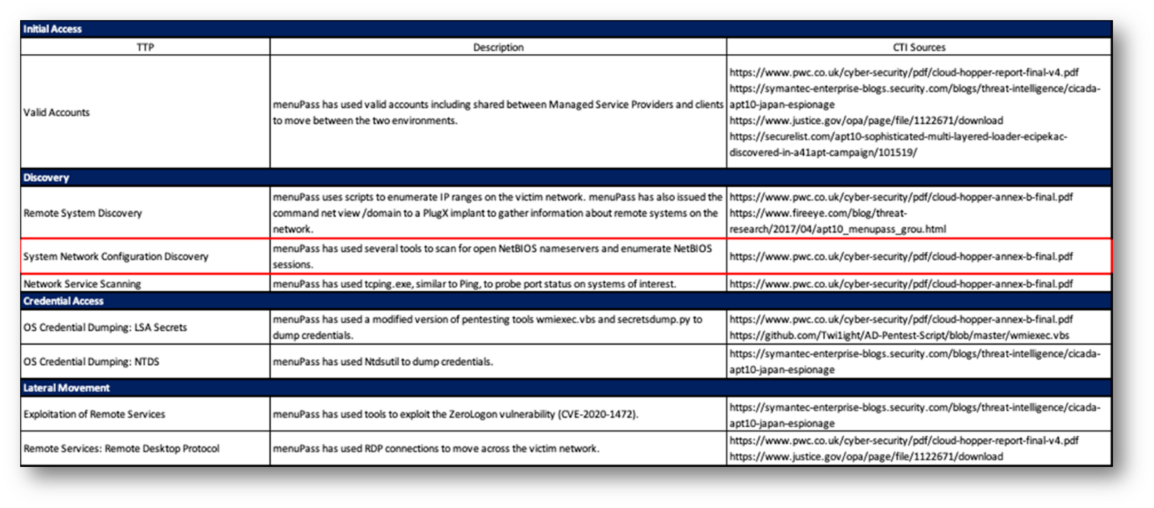
TTP Outline
After the testers finish defining their TTPs, they want to integrate them into an adversary emulation plan. This plan will be a step-by-step procedure for emulating adversary TTPs and will package all needed scripts, binaries, and tools to execute the plan.
Below is an example of a TTP outline.
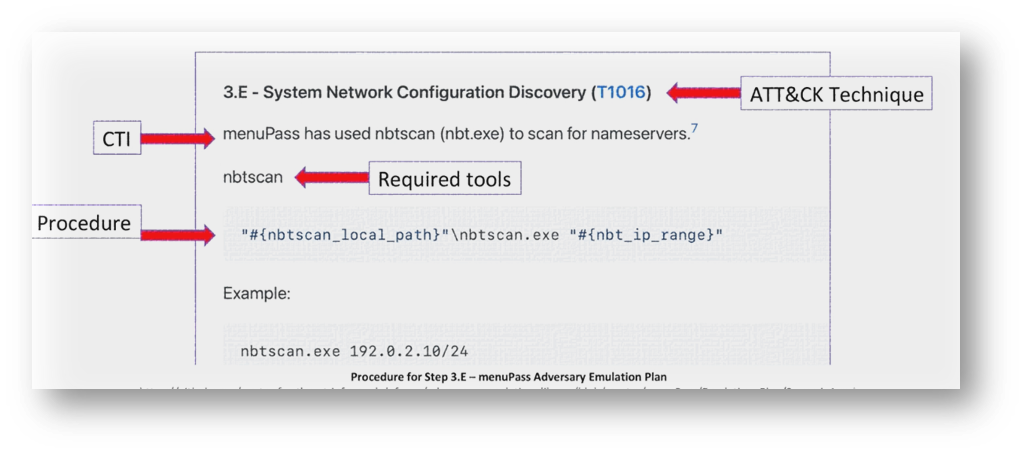
TTP Procedure
It’s important that the TTP procedure includes all resources needed to execute the TTP(s). However, this isn’t a rigid format, as many projects have their own conventions.
The figure below shows an example of the procedure for executing one or more adversary behaviors.
5. Conduct Simulation
By this point in the framework, the TTPs have been implemented into an adversary emulation plan. The pen testers are now ready to conduct the adversary emulation engagement, and this will look a little different for different organizations depending on what you want to test and how.
Execute Procedures
Execution entails running your TTPs against target systems. The pen testers have selected the techniques, will execute the techniques, and will review/ observe the results.
6. Report Results
Arguably, the most important aspect of adversary emulation is documenting your activities, findings, and recommendations. Documentation provides empirical proof of what you accomplished; it’s the record that network owners use to make decisions. Keep in mind that a good engagement with poor documentation is of minimal value.
Three forms of documentation you should expect from your threat simulation partner after the exercise occurs:
Operational Notes
Operational notes describe the testers’ activities during an engagement. The notes should answer who, what, when, why, and how. Keep command transcripts and logs, things you would expect from a penetration test report with a bit more rigor.
Professional Report
The professional report will include a description of engagement, objectives, scope, and some sort of narrative from the tester’s point of view.
Executive Presentation
If you have all of your operational notes and you have your professional report, this presentation should be fairly simple to put together in a way that is conducive to whatever audience the presentation is being presented to. Testing teams can gear the presentation towards executives if the board is being presented to, or they can make the presentation more technical if system admins or network defenders want this information.
Undergo Threat Simulation with KirkpatrickPrice
The threat landscape can be overwhelming to think about, especially since it’s constantly evolving. And although offensive security is a great way to stay on top of today’s threats, the process can feel scary because it’s essential that you work with someone you can trust. At KirkpatrickPrice, we have an offensive security team full of experts who care about helping you fortify your defenses against today’s threats. If you enjoyed this webinar recap, make sure to register for part two of our Threat-Informed Defense series that will cover purple teaming. Save your spot here!
In the meantime, if you’re looking to start a threat simulation exercise of your own or have questions about your environment, connect with one of our experts today.