
What are PCI Penetration Testing Requirements?
Nine new PCI DSS v3.2 requirements turned from best practices to requirements on February 1, 2018.
One requirement in particular, PCI Requirement 11.3.4.1, outlines new PCI penetration testing requirements and caused confusion among many service providers. PCI Requirement 11.3.4.1 states:
“If segmentation is used, confirm PCI DSS scope by performing penetration testing on segmentation controls at least every six months and after any changes to segmentation controls/methods.”
Let’s discuss why this PCI penetration testing requirement might apply to you, what segmentation is, what the six-month rule means, and what you need in order to comply with this requirement.
Does PCI Requirement 11.3.4.1 Apply to You?
There are two conditions as to whether or not PCI Requirement 11.3.4.1 applies to your organization.
- Are you a service provider? PCI Requirement 11.3.4.1 is an additional requirement that only applies to service providers. This is any entity that stores, processes, or transmits cardholder data on behalf of a third-party, or otherwise has the ability to impact cardholder data security.
- Do you use segmentation for the purpose of PCI scope reduction?
If both of these apply to you, all segmentation controls that are in place for the purpose of PCI scope reduction must be tested every 6 months or after any changes to segmentation controls or methods.
What is Segmentation and How Does It Impact PCI Compliance?
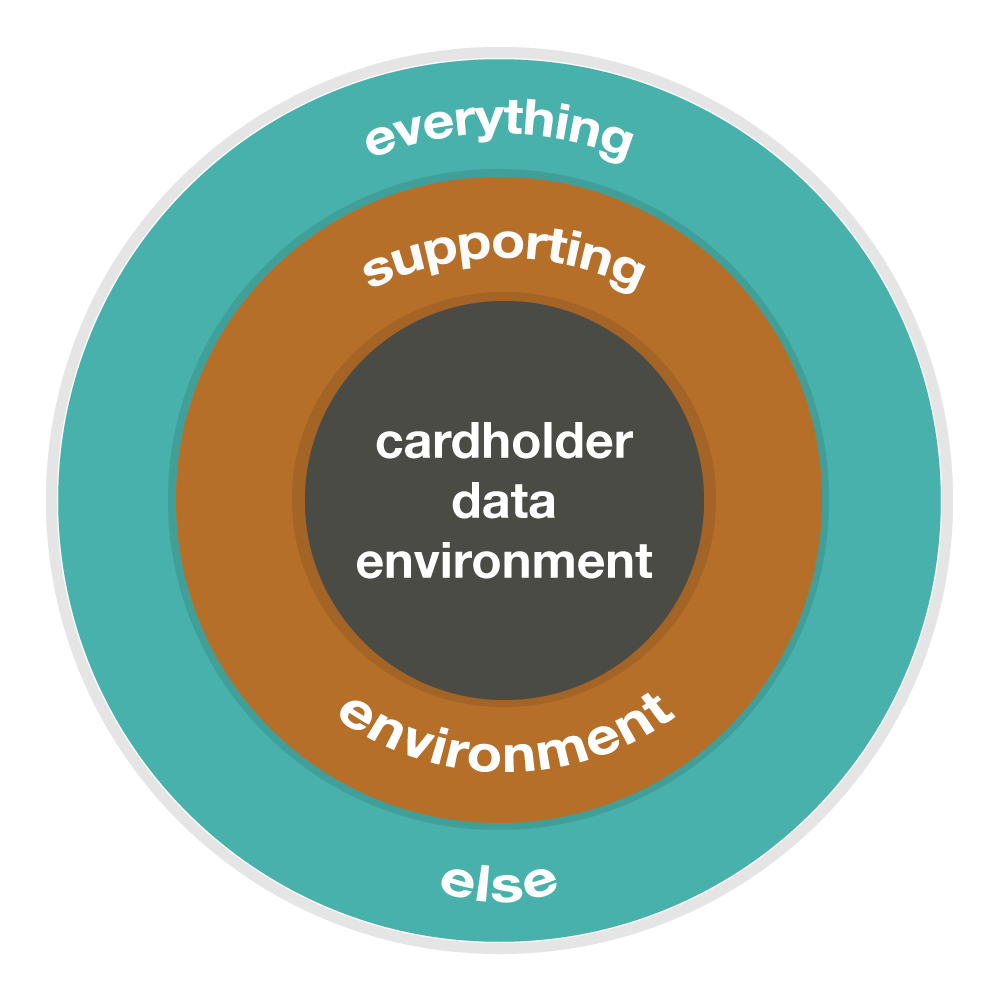
Think of your CDE as the center of a circle, with a protective, second circle surrounding it. This second circle is your supporting environment. This could include domain controllers, patch management systems, network and log monitoring systems and other similar devices that perform critical functions for systems located within the CDE.
These systems, which are connected to or impact the security of the CDE, are considered to be part of the overall PCI scope. Everything outside of the second circle should be segmented in order to reduce and tightly control the scope. This can reduce the cost and complexity involved with achieving and maintaining compliance with the PCI DSS.
What is PCI Requirement 11.3.4.1 Actually Requiring Regarding Penetration Testing?
PCI Requirement 11.3.4.1 requires that a penetration test, which validates the scope and effectiveness of segmentation controls, be performed every six months or after any changes to segmentation controls. The purpose of this additional penetration test is to ensure that segmentation controls continue to operate effectively throughout the year. The continual, complete isolation between CDE and non-CDE systems is key to your PCI compliance.
Our approach to compliance with PCI Requirement 11.3.4.1 involves more than simply validating segmentation controls through port scanning activities. The PCI DSS specifies that penetration testing must be performed, meaning that it is not sufficient to only perform something like nmap scans from non-CDE to CDE networks. Additional effort is required in order to meet this requirement for penetration testing, and our team of penetration testers is ready to help.
Our penetration testing requires some sort of discovery to verify that what we expected from the CDE is there. Using the background and understanding from the first penetration test, we must validate that the scope of your CDE hasn’t changed in the last six months. We must understand what was in the CDE six months ago and what’s in the CDE now. This establishes a baseline of healthy security of the CDE. If you don’t understand or know what’s on the inside of the CDE, how do you know that sensitive information can’t be seen from the outside?
Our PCI penetration testing efforts focus on wherever segmentation controls are lacking. Our testing includes confirmation of the effectiveness of applicable segmentation controls and performing many of the same internal penetration testing activities that are expected in order to comply with PCI Requirements 11.3.2 and 11.3.3. This comprehensive approach focuses on the entirety of the in-scope PCI environment and allows our penetration testers to effectively test the segmentation controls by leveraging information gathered during initial penetration testing to inform the approach used to attempt to circumvent the targeted segmentation controls.
Am I Overdue on PCI Requirement 11.3.4.1? How Soon Should I Expect to Perform Penetration Testing?
The PCI SSC has given some clarity on the six-month rule described in this requirement. If your organization is in panic mode thinking, “February 1 has hit and now we’re overdue on new PCI penetration testing requirements,” you’re probably not actually overdue.
The six-month rule went into effect the same day that the entire requirement went into effect. There’s no need to go back in time. If you had a penetration test performed in December 5, 2017, then your next penetration test should be scheduled for May 5, 2018.
The PCI DSS guidance explains, “For service providers, validation of PCI DSS scope should be performed as frequently as possible to ensure PCI DSS scope remains up to date and aligned with changing business objectives.”
How is your organization re-assessing its penetration testing needs?
If you have questions about how these PCI penetration testing changes will affect your compliance or need additional help with implementation, contact us today, download our on-demand webinar that reviews all nine new PCI DSS requirements, or check out our PCI Demystified series.
More PCI Compliance Resources
Beginner’s Guide to PCI Compliance
When Will You See the Benefit of an Audit?
More Penetration Testing Resources
Not All Penetration Tests Are Created Equal
How Can Penetration Testing Protect Your Assets?
Components of a Quality Penetration Test
Auditor Insights: Vulnerability Assessments vs. Penetration Testing




