
As many organizations are new to the HITRUST CSF, we receive a lot of questions regarding HITRUST CSF compliance. Certified HITRUST CSF Practitioner, Jessie Skibbe, has presented to us the top five frequently asked questions about HITRUST. Here are her answers:
Top 5 Frequently Asked Questions about HITRUST
I was just told that I need to be HITRUST certified by December 31, 2017. What should I do?
First, don’t panic, because KirkpatrickPrice is going to help you get through it. It’s important to keep in mind that on average, a Self-Assessment and Validated Assessment for certification will take you about four and a half months complete. It does require planning, and although there are certain things that can be shortened, there are a lot of time frames that you cannot shorten. For example, the Self-Assessment itself will likely only take 30-60 days, but after that you must allow time to remediate. The Validated Assessment takes 90 days, allowing a couple of weeks for Quality Assurance, and then four to six weeks for HITRUST to develop and complete the certification report. Be sure to keep those time frames in mind when working backwards to meet a deadline.
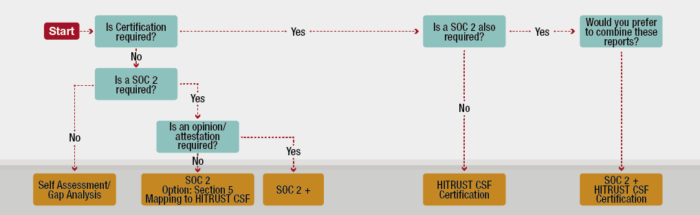
If I have a SOC 2 utilizing the HITRUST framework, is that the same thing as being HITRUST certified?
Not necessarily. There are three options when it comes to incorporating the HITRUST CSF into your SOC 2 report. The first option is just a SOC 2 using the Trust Services Principles. In this instance, we will list the mapping from HITRUST to the TSPs under Section 5 of the report. The second option is a SOC 2 +. In this option, the HITRUST CSF controls are incorporated into the body of the report. In this case, the CPA firm is issuing an opinion on overall HITRUST CSF compliance. This option does not include certification. The third, and final, option is a SOC 2 + HITRUST in which the SOC 2 incorporates the HITRUST CSF framework in addition to HITRUST certification. This is both a SOC 2 report and HITRUST CSF certification all in one. In this instance, certification is involved so the use of the MyCSF tool and HITRUST issuing the certification is required.
How many hours should I expect to invest on my end?
Keep in mind it takes about four and a half months to get through the Validated Assessment process, beginning with the Self-Assessment. To answer how many hours, it depends on where you are as far as your overall maturity. Do you have policies and procedures documented and in place? Do you need to implement any new controls? Starting with the Self-Assessment will give you a good idea of where your organization currently stands and where it needs to be.
How much should I expect this assessment to cost?
Depending on the type of assessment and report, fees will vary. A Self-Assessment (which you go through yourself using the MyCSF tool) will cost you about $2,500. A Validated Assessment requires you to engage with HITRUST as well as the assessor firm that is going to perform the assessment work. In this case, you will have fees coming from two different organizations. HITRUST fees start at $3,750. Fees are based on the number of users you want to have access to the MyCSF tool as well as things like your company’s annual revenue. As far as fees owed to the assessor, if you are a level 1 from an organizational and risk standpoint (service provider IT/non-IT), you can expect to pay around $10,000-$20,000. There are several varying factors that go into the amount of work that the assessor firm will need to accomplish. As we’ve mentioned before, the CSF is scalable, so you’ll need to work with your assessor firm to determine your scope and your true assessment cost.
I’m already compliant with PCI DSS. Do I still need to do the Self-Assessment? Or can I avoid doing the Self-Assessment?
No, you can’t avoid doing the Self-Assessment. There is a difference between PCI DSS and HITRUST CSF because HITRUST is a risk management framework and PCI DSS is a compliance framework. Whereas HITRUST is scalable and based on risk factors, PCI DSS is very compliance-focused and black and white. Although there may be a crossover between controls, the requirements are different and not all of the HITRUST CSF controls are covered in something like PCI DSS.
Hopefully our video series on Navigating HITRUST CSF Compliance has been helpful in preparing for your HITRUST compliance journey. If you need help getting started or have any further questions regarding HITRUST CSF Certification or building your relationship with HITRUST, contact KirkpatrickPrice today!
We get a lot of questions on HITRUST CSF compliance. That is why this last video, video #6 in our navigating HITRUST CSF compliance series, is all about those frequently asked questions. I’m Jessie Skibbe, Chief Compliance Officer with KirkpatrickPrice and Certified HITRUST CSF Practitioner. Let’s get started with those questions.
We commonly hear this: I was just told that I need to be HITRUST certified by December 31, 2017. What should I do? Well, first of all, you may want to panic just a little bit and then get over it, because we’re here to help you through this. The reason for a little bit of the panic is the time frame involved. Something to keep in mind is that on average, it’s going to take you at least four and a half months to get through the Self-Assessment and the Validated Assessment in order to get certified. It’s something that does require a little bit of planning. There are certain things that can be shortened, but there are some time frames that cannot be shortened. For example, you could probably get through the assessment in about 30-60 days (the Self-Assessment), but beyond that there is time to remediate, 90 days in total to complete the Validated Assessment, a couple of weeks in there for the Quality Assurance work, and then there’s four to six weeks for HITRUST to actually develop and complete the certification report (if certification is granted). Keep those time frames in mind when you’re working backwards towards a deadline.
The second question we most commonly receive is: If I have a SOC 2 utilizing the HITRUST framework, is that the same thing as being HITRUST certified? The answer to that is: not necessarily. There’s three options when it comes to incorporating the HITRUST CSF in your SOC 2 report. The first option is just a SOC 2 in itself, using the Trust Services Principles. In this situation, under Section 5 of the report which is an attested section, we can simply list the mapping from HITRUST over to the TSPs. This just serves to be informational to the people reading the report. Option number two is referred to as a SOC 2+. In this situation, the HITRUST CSF controls are brought into the body of the report. In this case, the CPA firm is issuing an opinion on overall HITRUST CSF compliance. This is again not certification. Only option #3 that I’m going to describe to you, which is a SOC 2 incorporating the HITRUST framework in addition to the HITRUST certification being attached or appended to the report. This is both a SOC 2 report and HITRUST certification all in one. In this situation, as I mentioned before, certification is involved, therefore use of the MyCSF tool and HITRUST issuing that certification is required. So only the last option would be considered HITRUST certification.
Another question we commonly get is: How many hours should I expect to invest on my end? Keeping in mind what we answered previously, if it takes about four and a half to five months to get through the Validated Assessment process (beginning with the Self-Assessment), it depends on where you are as far as your overall maturity. Do you have policies and procedures, or do you need to write those? Do you need to implement new controls? It really starts with that Self-Assessment to get a good idea of where you are and where you need to go. Until that Self-Assessment is performed, it’s tough to estimate exactly how many hours will be required.
The fourth question that I want to talk to you about today, and something that I would also be wondering if I was on your side, is: How much should I expect for the assessment to cost? Keep in mind that depending on the type of assessment report, fees are going to vary. A Self-Assessment report, which is something that you go through on your own using the MyCSF tool and really only maintain a relationship with HITRUST at that point unless you require or would like to have the assistance of an assessment firm, can be completed on your own using the MyCSF tool. That’s going to cost you about $2,500. In that situation, you get access to the MyCSF tool for 90 days and you also get a Self-Assessment report that helps you focus on where the gaps that you need to remediate are. Beyond that, you have the Validated Assessment. In the case of a Validated Assessment, you’re going to need to engage with HITRUST to receive a Validated Assessment report and you’re also going to need to engage with the Assessor firm that’s going to perform the assessment work; so, you have fees for the Validated Assessment report coming from 2 different companies. In that case, HITRUST fees start at $3,750. Fees range based on the number of users you want to have access to the MyCSF tool, as well as things such as your annual company revenue. You will want to contact HITRUST directly to get the fees associated with the Validated Assessment report. I can tell you from the Assessor point of view, giving you just a ballpark of what that would cost you; if you are basically a level 1 from an organizational and risk standpoint for a service provider IT/non-IT, you can expect to pay around $10,000-$20,000. I’m giving you a wide range because that are a lot of different varying factors that go into the amount of work that the Assessor firm will need to do. There are up to 845 requirement statements and that really varies based on the overall scalability of the CSF. You want to work with your Assessor firm, hopefully it’s KirkpatrickPrice, to get that scope nailed down to get the true assessment cost.
The last question that I commonly get is: I’m already compliant with PCI DSS. Do I still need to do the Self-Assessment? Can I avoid doing the Self-Assessment? I would say no. There’s a difference between PCI and the HITRUST CSF because HITRUST is a risk management framework, versus something like PCI DSS which is a compliance framework. Very different. HITRUST is scalable and based on risk factors. PCI is very black and white and very compliance-focused. Although there may be crossover between the controls, there’s very different requirements. Policy, Process (Procedure), Implemented, Measured, and Managed – the controls in place are very different. Not all of the HITRUST CSF controls are covered in something such as PCI.
That concludes our 6-part series on navigating HITRUST CSF compliance. I want to thank you for watching these videos. I really hope it was a valuable use of your time. We at KirkpatrickPrice really strive at educating, empowering, and inspiring our clients and we hope you enjoyed the content that we presented here. If you did enjoy the content, I strongly encourage you to subscribe to our channel. Also check out our website because it’s full of very useful content – blog posts that you can subscribe to, white papers that you can download – it’s all there and free for you. Please feel free to reach out to us directly at the contact information below. Again, thank you for joining us and I hope to see you again soon!



 CSF Security Assessment
CSF Security Assessment
 The very first thing organizations must do before downloading the
The very first thing organizations must do before downloading the