
When navigating your HITRUST CSF compliance journey, there are a few different assessment and reporting options to consider. But before you start the process of which HITRUST CSF assessment and report is right for you, it’s important to fully understand what your client is requesting. Have you received a letter from a client in the mail? Are you reviewing an RFP? The first question you must know the answer to is whether certification is required or not. Once you know what your client is asking for, you can determine your level of engagement with the HITRUST CSF and which assessment type makes sense based on your business objectives.
HITRUST Assessment Options
 CSF Security Assessment
CSF Security Assessment
The most common, and baseline, assessment option that organizations choose is the CSF Security Assessment. There are 66 controls that are required for HITRUST certification, and those are directly related to the CSF Security Assessment.
CSF Security Assessment + Privacy Assessment
There is an optional add-on for your CSF Security Assessment, and that is adding a Privacy component. If privacy is a concern of yours or applicable to your business, it will make sense to add the Privacy component to your CSF Security Assessment.
CSF Comprehensive Security Assessment
The CSF Comprehensive Security Assessment option evaluates all 149 controls, including the baseline 66 controls. Organizations will select this assessment option based on client demands. Maybe there will be someone internally, like a stakeholder, who wants to take a holistic approach to how your organization stands against the HITRUST CSF framework. This assessment option evaluates an organization’s information security management system against all the controls in the HITRUST CSF.
CSF Comprehensive Security + Privacy Assessment
Just like with the baseline CSF Security Assessment, there is an option to add a Privacy component to the CSF Comprehensive Security Assessment.
NIST Cybersecurity Assessment
If the NIST Cybersecurity Framework is applicable to your organization, you also have the option to evaluate the HITRUST CSF requirement statements that pertain to the NIST Cybersecurity Framework with the NIST Cybersecurity Assessment option.
HITRUST CSF Report Options
There are several options for demonstrating your compliance with the HITRUST CSF framework. These options include:
- SOC 2
- SOC 2 +
- SOC 2 + HITRUST CSF Certification
- HITRUST CSF Self-Assessment
- HITRUST CSF Validated Assessment (Certification)
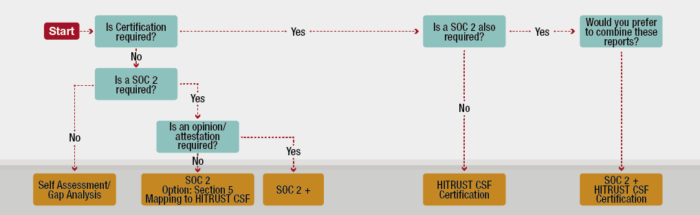
Some of your clients may accept a HITRUST CSF Self-Assessment only, as a Self-Assessment Security Assessment might satisfy the OCR’s requirements for a HIPAA risk analysis since it’s a risk-based compliance framework. A Self-Assessment is a great way to begin your HITRUST compliance efforts, and is what KirkpatrickPrice recommends to clients who are just starting out. To begin a HITRUST CSF Self-Assessment, you must establish a relationship with HITRUST, log into the MyCSF tool, and select the self-assessment option. A Self-Assessment must be completed within 90 days and results in a finalized report. This option doesn’t provide the highest level of assurance since it is based on your own evaluation and attestation of your organization’s compliance.
A Validated Assessment provides a greater level of information security assurance and is performed by an approved CSF Assessor, like KirkpatrickPrice. Validated assessments include a HITRUST CSF Self-Assessment in which you answer questions and attest to your compliance, followed by a CSF Assessor validating your controls against what you have said is in place.
Once you have decided which assessment type and level of engagement is right for you, you need to know which report is required. A few years ago, HITRUST and the AICPA came to an agreement that the HITRUST CSF framework itself can be used within a SOC 2 Report. In some instances, your client may ask you for either HITRUST CSF Certification or a SOC 2 only. In other cases, depending on if you service different industries, you may have clients that ask for both. In this case, it would benefit most organizations to utilize the HITRUST CSF within the SOC 2 framework, satisfying both. It’s important to remember that clients who are asking for HITRUST CSF Certification will not be satisfied with a SOC 2 only, and you must have the certification element if that is what your client is requiring.
Understanding which HITRUST CSF assessment and report option your clients will accept is key. Contact me at s.morris@3.95.165.71 for more information on which assessment and report type is right for your organization.
Hello, this is Jessie Skibbe, Chief Compliance Officer with KirkpatrickPrice. We’re here today to continue our video series of navigating HITRUST CSF compliance. To take you back to where we’ve been, we started off with video #1 in the series, talking about who HITRUST is, what the CSF is, and what it aims to solve as far as problems in the healthcare industry. In video #2, we started digging deeper and deeper into the CSF itself, helping you determine how to establish scope and how to navigate the controls in greater detail. Today, I want to talk about the assessment options that you have.
You have assessment options and then you have report options to consider. Before you start this process of trying to determine which is right for you, it’s really important to know what your client is requesting. If you are a Business Associate pursuing HITRUST certification or HITRUST compliance, you must understand what your client is asking for. If you’ve received a letter in the mail or if you have been reviewing an RFP that you’re applying for, you must understand if certification is required. That’s first and foremost the important step.
Out of the assessment options that you have, the most common assessment option is the CSF Security Assessment option. That’s what I’ve been referring to all along in this video series as the requirement for certification. There’s 66 controls right now required for HITRUST certification and those are related to the CSF Security Assessment.
The optional add-on, option #2, is the CSF Security + Privacy Assessment. If privacy is a concern of yours or applicable to your business, you may want to select the Security + Privacy option.
The third on the list of assessment options is the CSF Comprehensive Security Assessment. The difference between Comprehensive and Security is that Comprehensive covers all 149 of those controls; beyond that subset of the 66, it covers all 149. The reason for choosing a Comprehensive Assessment may be because your client demands it, although that hasn’t been the norm of what we’ve seen. It may be a situation where someone internally, like a CEO or investment partners, may want to know from a holistic view how you’re doing comprehensively according to the framework. They would want your information security management system to be evaluated against all 149 controls.
Beyond that, you can choose the CSF Comprehensive Security + Privacy Assessment. Again, adding that Privacy component onto that Comprehensive Assessment.
The next option would be if the NIST Cybersecurity Framework applies to you. That seems not to be the common element, but it is an assessment option that’s available to you.
The assessment options will apply whether or not you’re pursuing a Validated Assessment or whether you’re pursuing a SOC 2. Let’s dig deeper into the report options. Once you decide which assessment option is right for you, you need to know what report is required. Some of your clients may accept what’s called a HITRUST CSF Self-Assessment. A HITRUST CSF Self-Assessment, for example, may satisfy the OCR’s requirements for a risk assessment, given it is a risk-based compliance framework. Keep that in mind because a Self-Assessment is an excellent way to begin with your compliance efforts. In fact, that’s what we recommend, to always start with a Self-Assessment. If the Self-Assessment happens, you establish a relationship with HITRUST, you log into the My CSF tool, and you select the Self-Assessment option. The Self-Assessment must be completed within 90 days. It’s all based on your input and your evaluation of controls. What comes out of that is a HITRUST CSF Self-Assessment Report. A Self-Assessment, of course, is not the highest level of information security assurance because it’s all based on how you are evaluating yourself.
The next option, the HITRUST CSF Validated Assessment, is a greater level of information security assurance. In that case, you would hire someone who is a CSF Assessor firm, very much like KirkpatrickPrice, to validate your controls against what you have said is in place. A Validated Assessment is just that; it’s you entering information, it’s you attesting to your compliance, and then it’s someone coming in to validate that.
Another report option to consider is a SOC 2. A couple of years ago, the AICPA and HITRUST came together and came to an agreement that the HITRUST framework itself could be utilized within a SOC 2 report. In some cases, your client may ask you for either certification or a SOC 2; they may ask for either/or. Some of the benefits of having a SOC 2 that uses the HITRUST framework is that you may have some clients that ask for both. Maybe some of your clients are in financial services, other clients are in healthcare. Having a SOC 2 performed using the HITRUST framework could satisfy both, but keep in mind that those clients asking for HITRUST certification will not be satisfied with a SOC 2 using HITRUST components. You have to have that certification element if your client is requiring it. In that case, you could do the SOC 2 and then the HITRUST certification could be added to that as an additional component of the SOC 2. There’s lots of different options as far as the assessment types and the report options. Knowing which is right for you is the first step in determining what your next step in your overall compliance objectives should be. This concludes our overview of assessment types and report options. To further assist you in deciding which is right for you, we’ve put together the graphic that you’re seeing now. As you can see, at the starting point is really knowing if certification is required. If certification is required, then navigating the rest of the options is fairly simple. It’s the first question that we would ask you if you called our firm and asked for assistance. We’d want to know if your client is asking for certification or not. Something that you need to know and remember is that if certification is required, HITRUST is the only entity that can issue certification directly; a 3-way relationship must exist. We have a relationship as a CSF Assessor firm with HITRUST, you have a relationship with HITRUST from using the My CSF tool and requesting that HITRUST CSF Validated Assessment Report, and then we have a relationship with you as our client. That relationship has to be established because HITRUST is the only entity that can issue certification. That word – certification – is always step #1. Knowing if that is required should be the first thing you get an answer to.
In our next video, we’re going to talk about how the scoring mechanism works within the control framework. If a Validated Assessment is chosen and you want to receive certification, you must understand the maturity model and how controls are scored in order to know if you’re going to meet the certification requirements. I hope you’ll join us for our next video! If you need any further information or need assistance immediately, please contact us at the link below.

 The very first thing organizations must do before downloading the
The very first thing organizations must do before downloading the 

